Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
Offensive And Defensive Security: Safeguarding Your Digital World

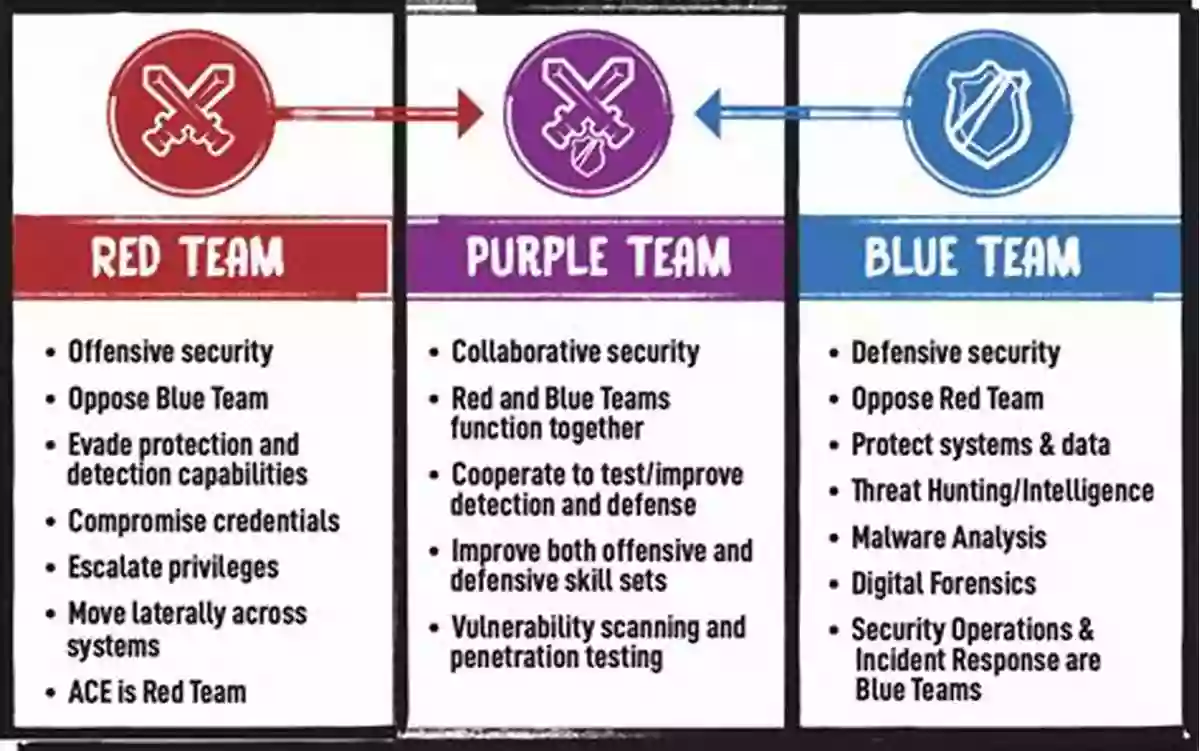
In today's interconnected world, where digital threats lurk around every virtual corner, it has become imperative to implement effective offensive and defensive security measures. With cybercriminals constantly devising new and sophisticated ways to exploit vulnerabilities, individuals and organizations must stay vigilant to protect their sensitive information, networks, and online presence. This article takes an in-depth look at offensive and defensive security, highlighting their significance and providing insights into effective strategies to safeguard your digital world.
Offensive Security
Offensive security, also known as ethical hacking or penetration testing, involves actively identifying and exploiting vulnerabilities in an organization's systems, applications, or networks. This practice is not meant to harm or steal data but rather to assess vulnerabilities from the perspective of a potential attacker. Conducting offensive security testing helps uncover weaknesses before malicious actors do, allowing organizations to patch vulnerabilities and enhance their overall security posture.
4.1 out of 5
| Language | : | English |
| File size | : | 13691 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 458 pages |
Offensive security professionals, also known as white-hat hackers or security researchers, employ various techniques to uncover vulnerabilities. These may include network scanning, phishing simulations, social engineering, or code review. By attempting to infiltrate systems or networks, offensive security specialists help organizations identify weaknesses and develop better defense mechanisms against cyber threats.
Defensive Security
Defensive security, on the other hand, centers around preventing and mitigating cyber threats by implementing protective measures. It involves building a robust security infrastructure, developing policies and procedures, and employing technologies that safeguard against attacks.
Core elements of defensive security include firewalls, intrusion detection and prevention systems (IDPS),encryption, secure network configurations, employee education and awareness, and regular security audits. By implementing these measures, organizations can minimize risks and protect their valuable assets from unauthorized access, data breaches, or service disruptions.
Effective Offensive and Defensive Security Strategies
Combining offensive and defensive security strategies maximizes the chances of safeguarding against a wide range of cyber threats. Here are some effective strategies for implementing offensive and defensive security:
1. Regular Vulnerability Assessments
Conduct regular vulnerability assessments to identify weaknesses within your systems and networks. Utilize industry-standard tools and methodologies, or consider hiring a professional penetration testing team to uncover and address vulnerabilities.
2. Implement Intrusion Detection and Prevention Systems (IDPS)
Deploy IDPS solutions to monitor network traffic and detect potential intrusions or anomalies. These systems can automatically block suspicious activities and provide real-time alerts, helping prevent unauthorized access or attacks.
3. Develop and Enforce Strong Security Policies
Establish comprehensive security policies that outline best practices for data protection, network configurations, password management, and employee responsibilities. Regularly communicate and enforce these policies to ensure a secure work environment.
4. Conduct Regular Security Awareness Training
Educate employees about common cyber threats, such as phishing attempts, social engineering, or malware. By raising awareness, employees become a strong line of defense against potential attacks and are more likely to adhere to security protocols.
5. Secure Remote Access and Mobile Devices
With the increasing trend of remote work and BYOD (Bring Your Own Device),organizations must secure remote access and mobile devices. Implement two-factor authentication, enforce secure VPN connections, and utilize mobile device management solutions to ensure data security on mobile devices.
6. Continuously Update and Patch Systems
Regularly update and patch operating systems, applications, and firmware to address known vulnerabilities. Cybercriminals often exploit outdated software, and timely updates help protect against known threats.
7. Establish an Incident Response Plan
Prepare and document a detailed incident response plan to effectively handle cybersecurity incidents, minimizing potential damages. This plan should outline roles, responsibilities, communication channels, and recovery procedures.
8. Monitor and Analyze Logs
Implement a centralized log management system to collect and analyze logs from various systems and applications. Monitoring logs allows for the early detection of suspicious activities and enables swift response to potential security breaches.
Offensive and defensive security measures form the backbone of a robust cybersecurity strategy. By actively identifying vulnerabilities through ethical hacking and implementing protective measures to safeguard against attacks, individuals and organizations can mitigate risks and enhance their overall security posture. While there is no foolproof security solution, a proactive approach backed by continuous monitoring, regular assessments, and employee education acts as a strong deterrent against cyber threats. By prioritizing offensive and defensive security, you can create a safer digital world for yourself and your organization.
References:
[Add references here]
4.1 out of 5
| Language | : | English |
| File size | : | 13691 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 458 pages |
Numerous publications exist which examine elements of the security discipline. Few address these elements as a continuum of interrelated functions. None examine the structure of Offensive vice Defensive security in anything other than the domain of international security . This text has been written to fill this gap and to support a course in Offensive-Defensive Security, developed by Henley-Putnam University, which briefly reviews the history of the field of strategic security and its three component parts protection, intelligence, and counterterrorism as well as its two distinguishing characteristics: offensive tactics and operations combined with technological innovation.
The course then moves to an in-depth assessment of related security areas that focus on defensive tactics and operations: homeland security, criminal justice, conflict and peace studies, and emergency management. While these fields may appear at first to be part of strategic security, this course and the associated text explores the critical differences and the fact that they are also critical elements of industrial, governmental, and military security. Emphasis will be placed at an introductory level both academic and professional distinctions and discuss the structures associated within these domains.
The text is divided into the following key sections:
Section 1: The Basics
Section 2: The Environment
Section 3: Security Planning and Management
Section 1 provides an orientation for the reader to a common frame of reference through information provided in the following chapters. It is not intended to be a single source of all relevant information. Additionally, this text is not intended to be the exhaustive single source for all conditions. Rather, it provides a roadmap of considerations on how to reach a specific goal in an efficient and informed manner.
Section 2 examines the world the security professional must inhabit, again, in a generalized manner and, likely, in a way never before considered. Elements of neurology, biology, physics, philosophy, logic, analytics, and finance are presented in a manner unique to the changing paradigm of Offensive-Defensive Security philosophy. The various chapters are labeled as terrains as the best representation of the environmental information to be discussed. Each will approach the topics in as clear a manner possible of current thinking and science within each as critical to the understanding of the total security environment; the how, why, and in what ways they will affect the world of this security paradigm.
Finally, Section 3 incorporates the information of the first two sections and applies the knowledge gained to the planning and management of an integrated security plan. The objective of this section is to utilize the concepts and processes developed via international agencies such as the Project Management Institute to demonstrate how to create an integrated and manageable enterprise structure and not a one-size fits all template.
As the knowledge consolidates, integration begins, that of incorporating the security entity into the enterprise as a whole be that enterprise be a business, government entity, or military operation. The only difference is the scale. This is a vital step in that the act of protection cannot interfere with the process of performing the enterprise function. In fact, it must enhance the enterprise function and assist in ensuring its success.
Key Learning Points
The approach and purpose of this text has been outlined. The following are the key reasons or learning points in summary.
a.Define the key elements and environments within which the security plan and operational management activities must occur
b.Familiarize the student with cultural, biological, financial, informational, and legal aspects necessary for the understanding of how these domains influence human behavior; the primary aspect of security planning and operations
c.Familiarize the

 Richard Simmons
Richard SimmonsThe Secrets of Chaplaincy: Unveiling the Pastoral...
Chaplaincy is a field that encompasses deep...

 Manuel Butler
Manuel ButlerAnimales Wordbooks: Libros de Palabras para los Amantes...
Si eres un amante de los animales como yo,...

 Rod Ward
Rod WardLet's Learn Russian: Unlocking the Mysteries of the...
Are you ready to embark...

 Rod Ward
Rod WardThe Incredible Adventures of Tap It Tad: Collins Big Cat...
Welcome to the enchanting world of...

 Eugene Powell
Eugene PowellSchoolla Escuela Wordbookslibros De Palabras - Unlocking...
Growing up, one of the most significant...

 José Martí
José Martí15 Exciting Fun Facts About Canada for Curious Kids
Canada, the second-largest...

 Ken Simmons
Ken SimmonsWhat Did He Say? Unraveling the Mystery Behind His Words
Have you ever found yourself struggling to...

 Carlos Fuentes
Carlos FuentesA Delicious Journey through Foodla Comida Wordbookslibros...
Welcome to the world of Foodla Comida...

 Matt Reed
Matt ReedThe Many Colors of Harpreet Singh: Embracing...
In a world that often...

 Chandler Ward
Chandler WardWelcome To Spain Welcome To The World 1259
Welcome to Spain, a country that captivates...

 Garrett Powell
Garrett PowellAmazing Recipes for Appetizers, Canapes, and Toast: The...
When it comes to entertaining guests or...

 Emilio Cox
Emilio CoxDays And Times Wordbooks: The Ultimate Guide to Mastering...
In the realm of language learning,...
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Ivan TurgenevUnlocking the Secrets of Efficiency, Complexity, and Resilience in Signal...
Ivan TurgenevUnlocking the Secrets of Efficiency, Complexity, and Resilience in Signal... Stephen FosterFollow ·18.5k
Stephen FosterFollow ·18.5k Kirk HayesFollow ·8.7k
Kirk HayesFollow ·8.7k W.H. AudenFollow ·11k
W.H. AudenFollow ·11k Leo MitchellFollow ·19.5k
Leo MitchellFollow ·19.5k Bryce FosterFollow ·6k
Bryce FosterFollow ·6k Devin RossFollow ·8.9k
Devin RossFollow ·8.9k Stephen KingFollow ·17.4k
Stephen KingFollow ·17.4k Quentin PowellFollow ·19.2k
Quentin PowellFollow ·19.2k




















